Configure AWS Cloud account
In this section, you will find a guide on how to configure your AWS Cloud Account.
To deploy your applications on StackSpot, configure a cloud account within your Workspace. But first, you need to delegate access between AWS accounts using IAM roles to grant StackSpot access to your account profile.
Follow these steps to connect your AWS account:
Prerequisites
- Access to the AWS console;
- Access to a Workspace;
- An environment within your Workspace;
- Permission to manage Cloud accounts in your StackSpot account:
cloud_services:manage_cloud_account. See how to customize Roles and Permissions in your StackSpot Account. - Permission to manage IAM.
The configuration and addition of Cloud accounts in StackSpot in this manner are only available for:
- Enterprise Accounts created before 2024.
For Enterprise Accounts created from January 2024 onwards, the Cloud accounts must be connected via Self-hosted.
Step 1. Create IAM role
From the Amazon AWS page:
- Log in to your AWS Account;
- In the top left menu, click on the 'Services' button and then 'All Services';
- Navigate to IAM (Identity and Access Management)' in the list;
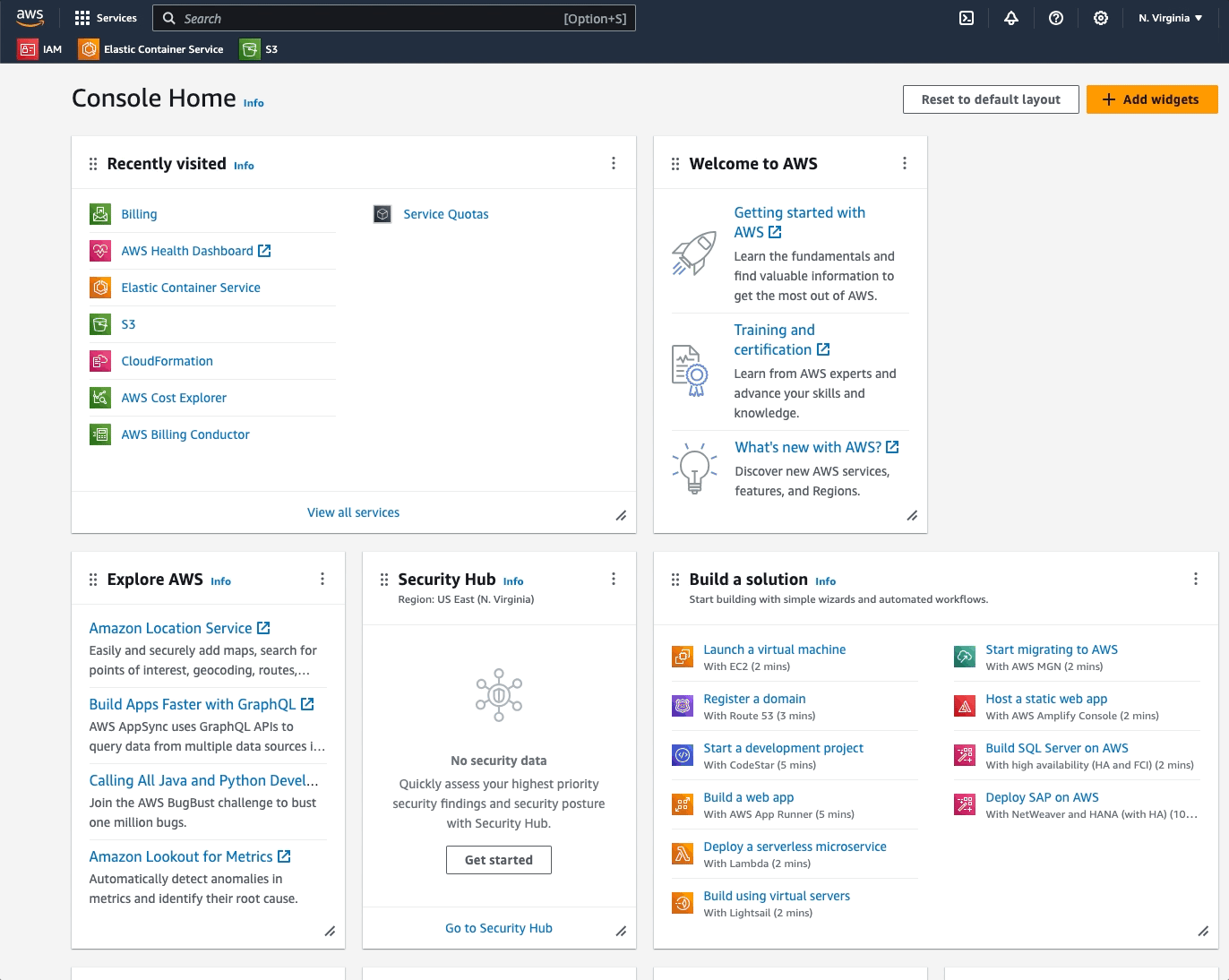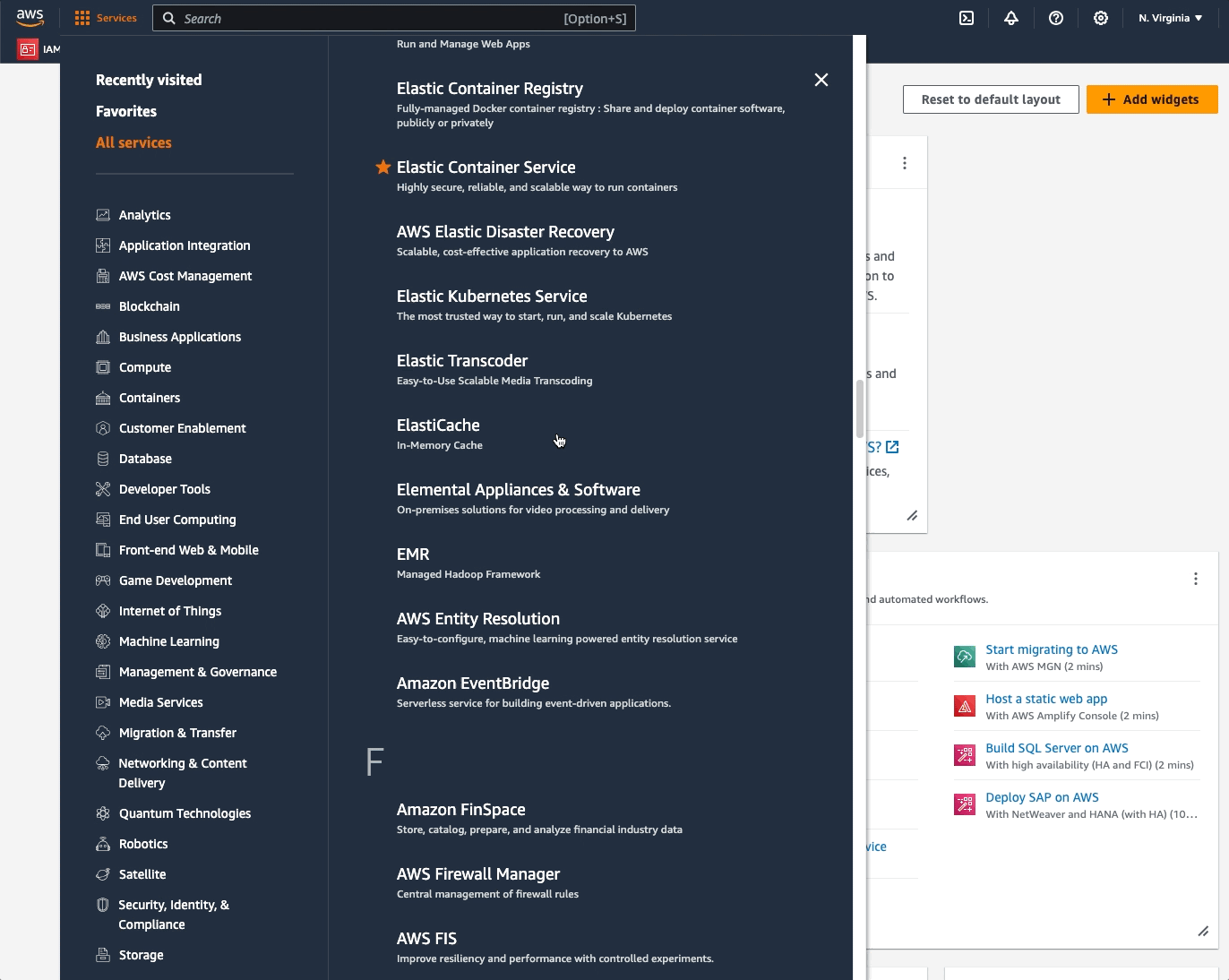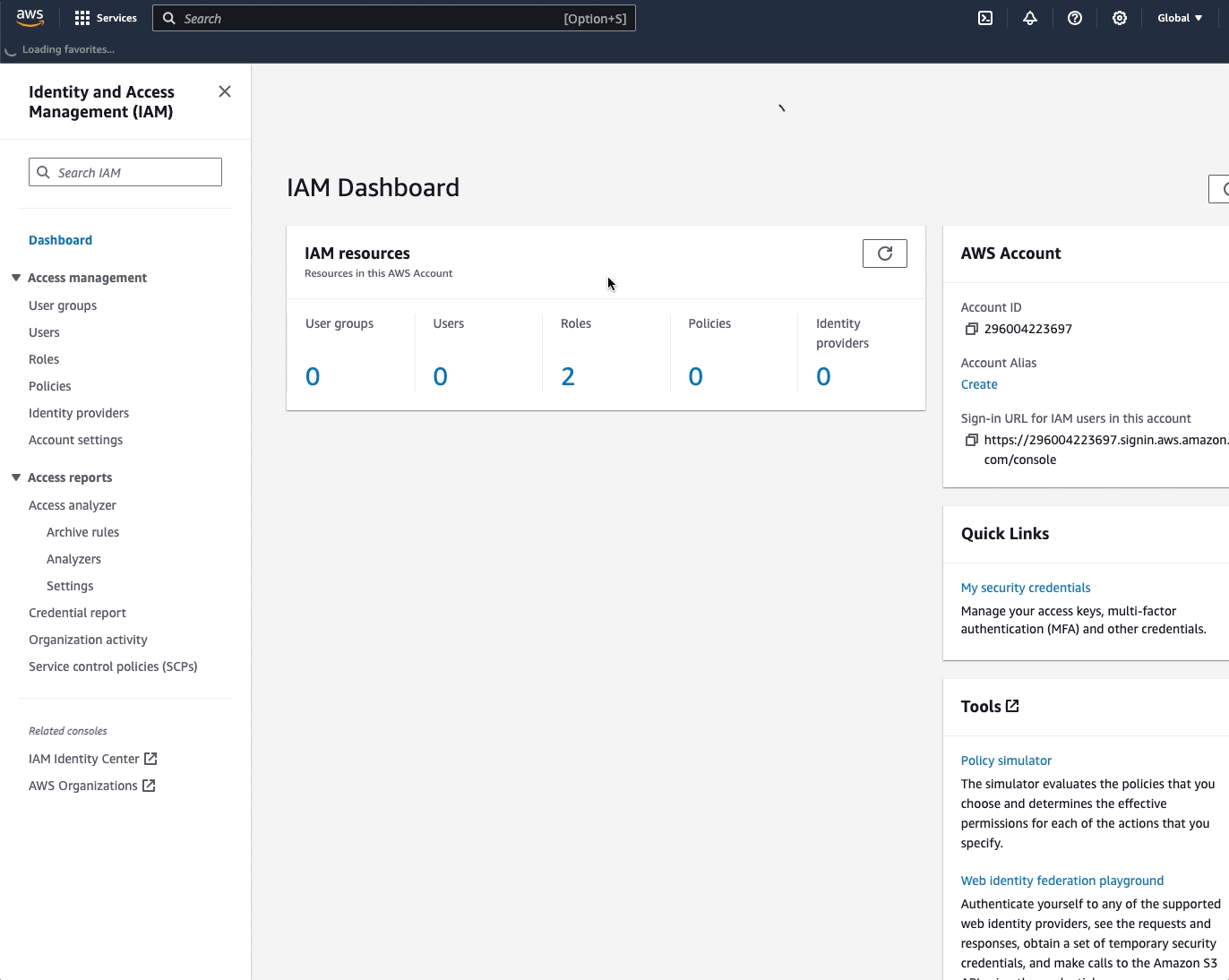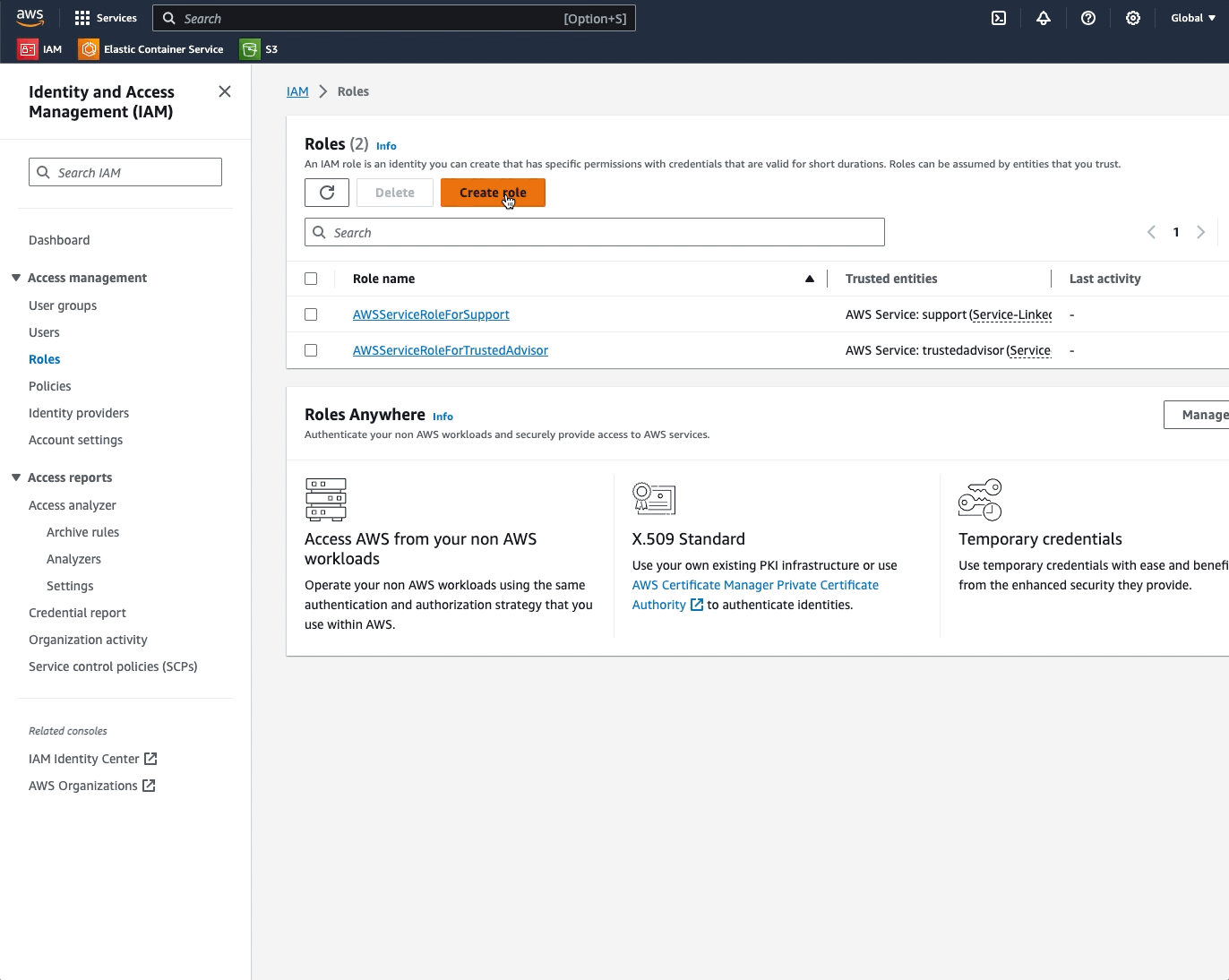
- In the left-side panel, under the 'Access Management' menu, select 'Roles';
- On the 'Roles' screen, click on the 'Create role' button;
- On the 'Select trusted entity' screen, under 'Trusted entity type' select the 'AWS account';
- In the 'An AWS account' section select the 'Another AWS account' option:
- Enter the StackSpot AWS account ID.
742799255367
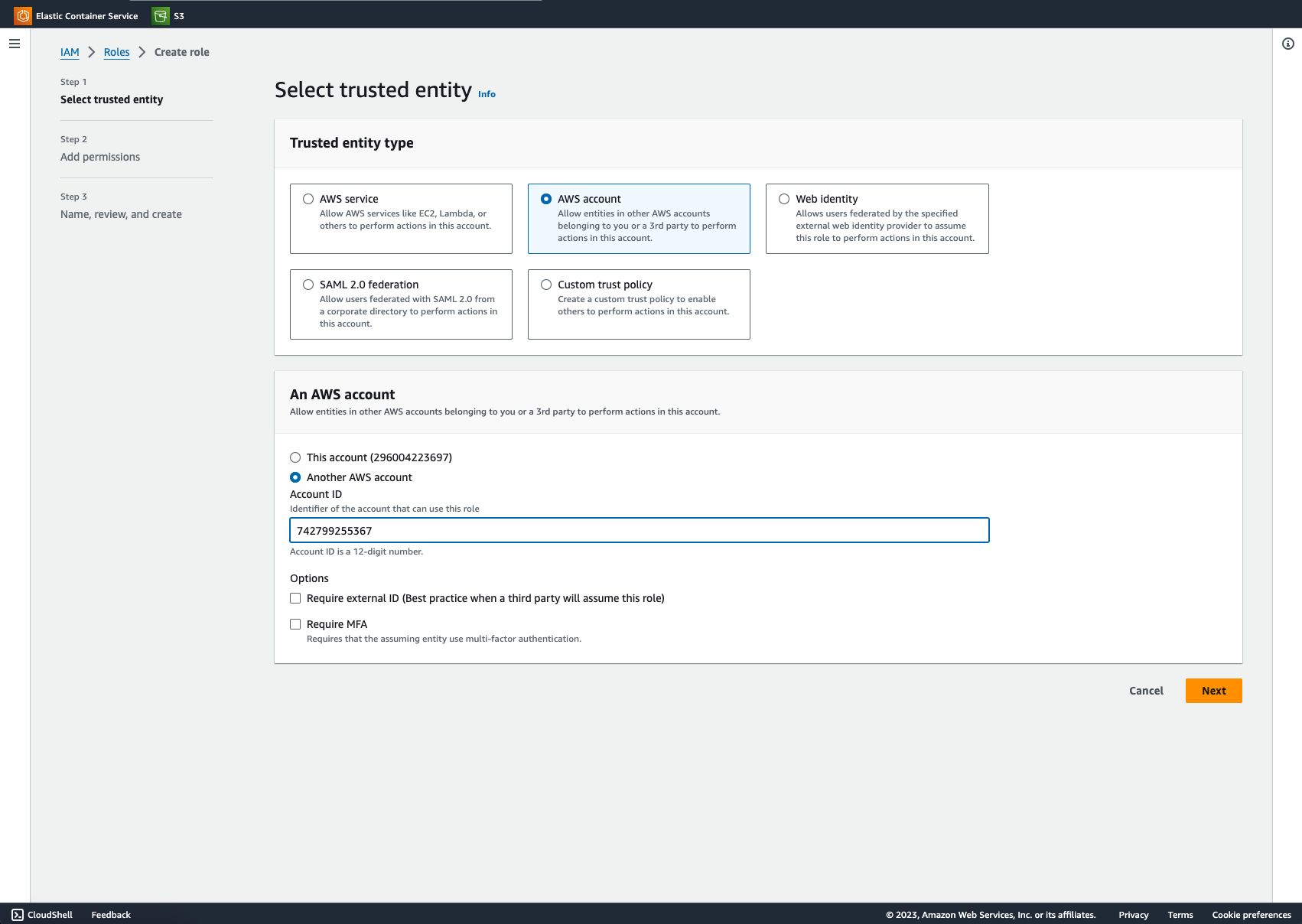
The account ID is a 12-digit number. Then click 'Next';
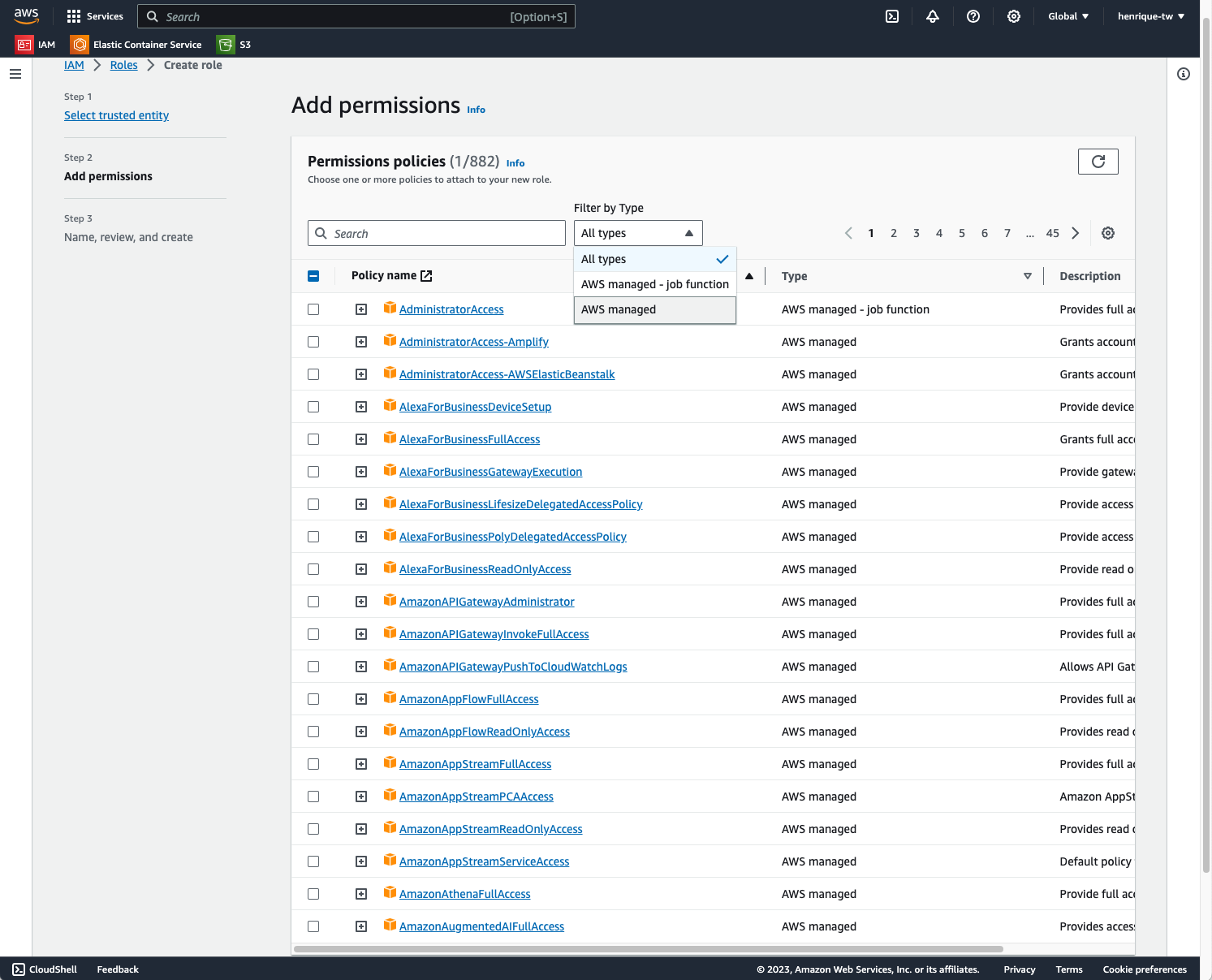
- On the 'Add permissions' screen, choose the necessary policies for your cloud resource, then click 'Next';
- On the 'Name, review, and create' screen, fill out the following fields:
Role name: Enter a meaningful name to identify this role; Description Add a brief explanation of this function. Ensure that the trust policy includes the AWS StackSpot account ID and permissions, as in the example below:
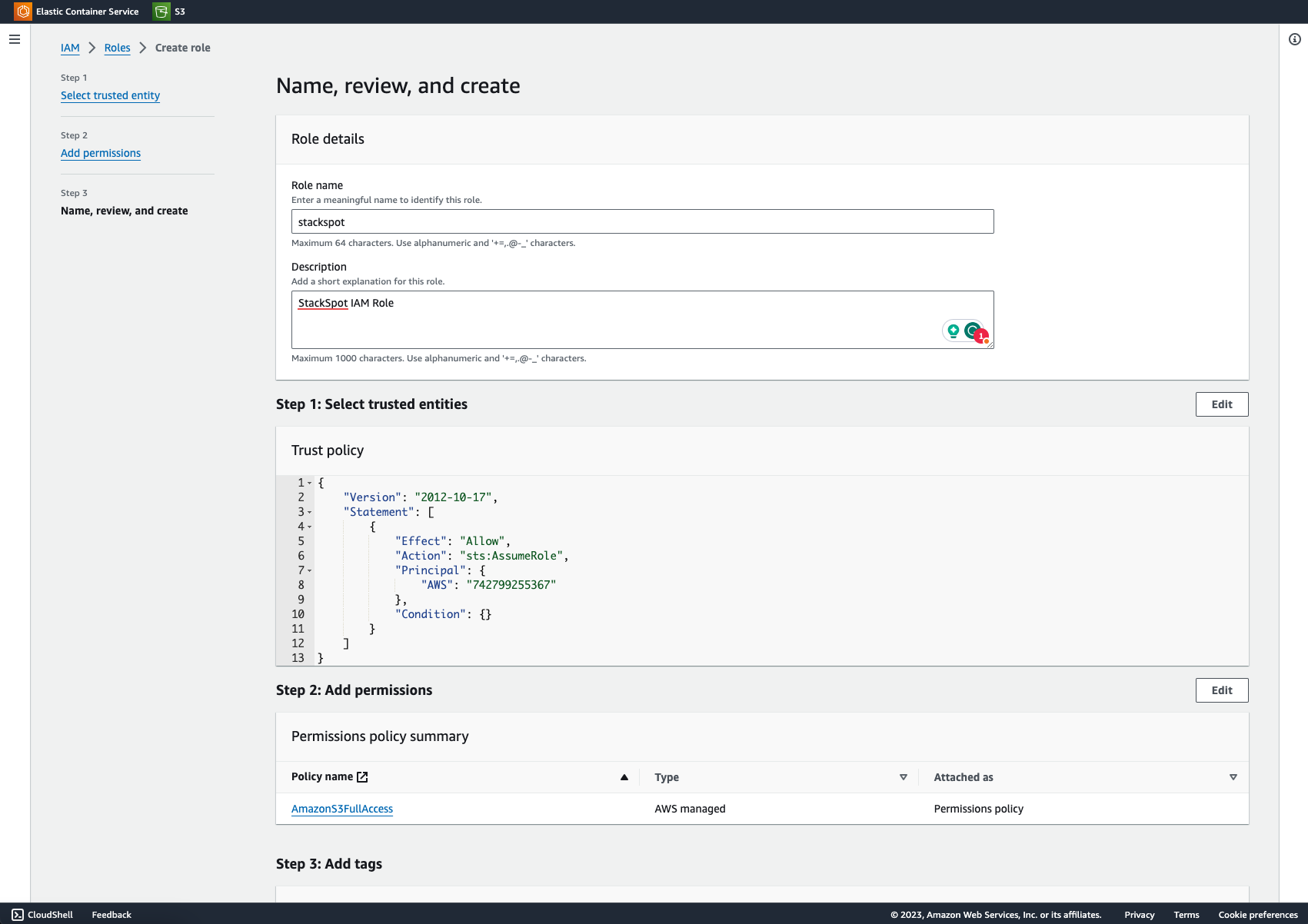
Click 'Create role' ;
- You will be redirected to the list of roles; locate the created role and click on it. Find and save the
ARNnumber on the role Summary screen.
- On the role Summary screen, locate and save the
ARNnumber. - In the 'Trust relationships' tab, click on 'Edit trust policy' and replace the current JSON with the following code:
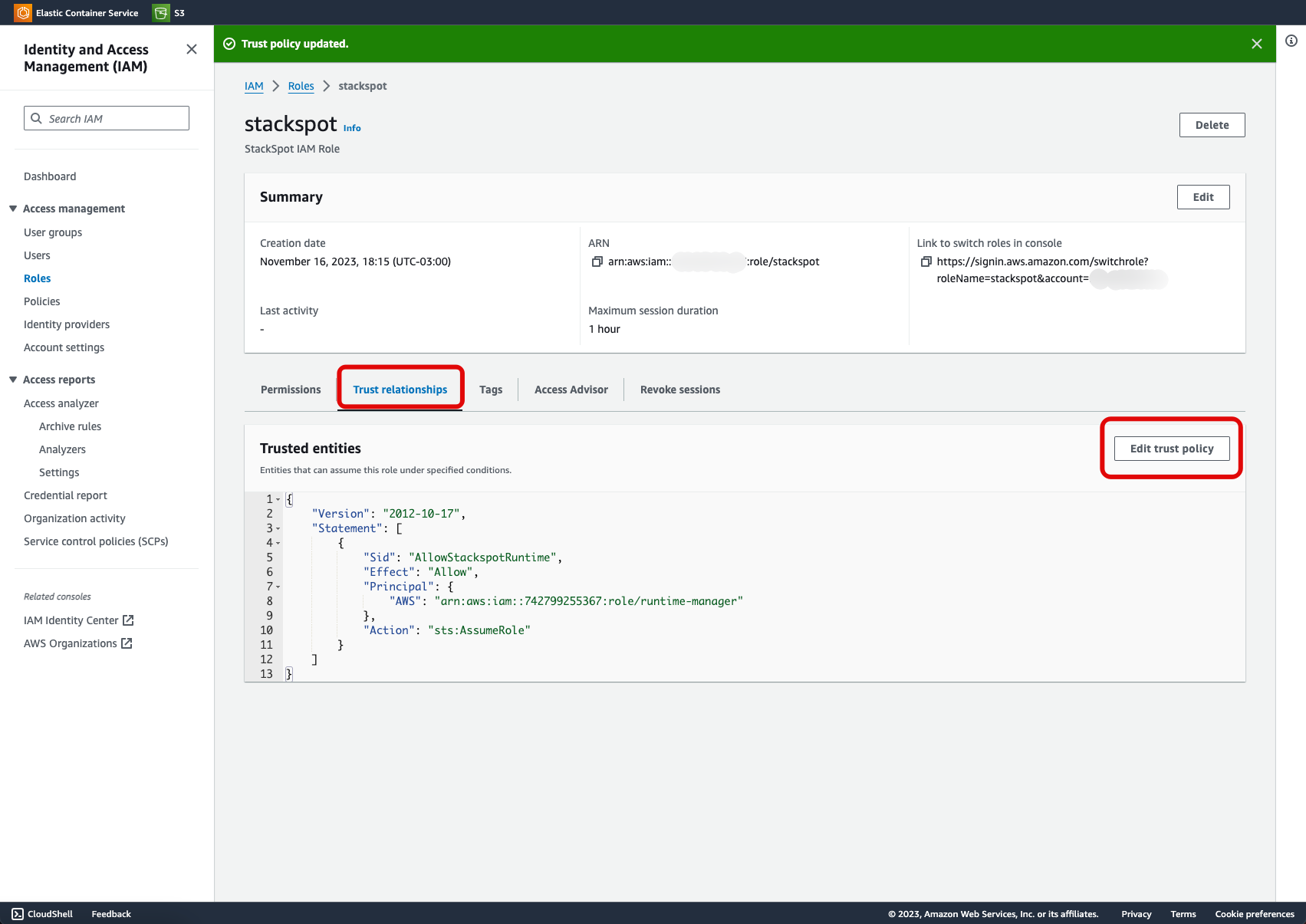
The AWS role: "arn:aws:iam::742799255367:role/runtime-manager" will be deprecated, if you still use this role, change it to ""arn:aws:iam:: 742799255367:role/stackspot"" as in the example below.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowStackspotRuntime",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::742799255367:role/stackspot"
},
"Action": "sts:AssumeRole"
}
]
}
Step 2. Connect your account to your Workspace environment
From StackSpot:
- Log in to the Platform;
- Access your Workspace;
- In the left-side menu, under Settings, click on 'Cloud accounts';
- Locate the environment you will use and click 'Connect cloud';
- Enter the ARN generated in the function creation. Then click 'Next';
- Review the data and click the 'Connect Cloud' button.
Disconnect cloud account
- Log in to login to the platform;
- Access your Workspace;
- In the left side menu, in Settings, click on “Cloud Account”;
- Select the environment where you want to disconnect the cloud account and click:
- Disconnect Cloud Account to disconnect the desired environment;
- Disconnect All to disconnect all environments from that Workspace.
Each environment has the information 'Connected' when it has a connected cloud account or Disconnected when there is not.
Next step
- Deploy your Application, see the Deploy section.